Project Details
- Project Name: NMS
- Clients: -
- Category: Software and Hardware
- Project Year: 2019
Nephila Network Solution
Today, each business depends on a computer and network infrastructure for the internet, internal management, telephone, and email. A complex set of servers and network equipment is required to ensure that business data flows seamlessly between employees, offices, and customers. The economic success of an organization is tightly connected to a hitch-free flow of data. In this way, The Developy has developed ARGINIX for network monitoring and management solutions for 7/24 monitoring and reporting.
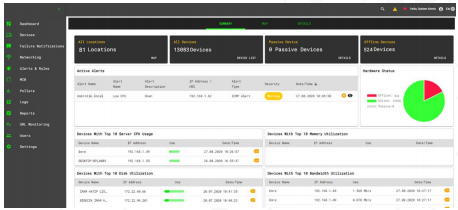
Dashboard
The Dashboard provides an overview of the device statuses in the system. Arginix provides dashboards that make it easy for the user to obtain system summary without having to decipher complex graphs and tables.
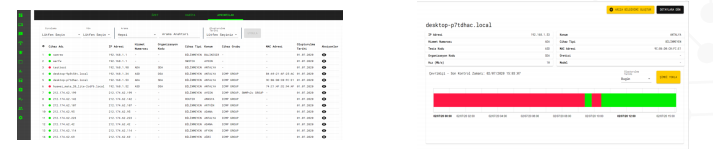
Maps
In the Map Module, system devices are shown on the selected country map. Selected device inventory information can be exported.
Device Details
SNMP v1, SNMP v2, SNMP v3, ICMP, TELNET, SSH, WMI, RPC protocols and all known devices regardless of brand are successfully employed and monitored. Inventory information of all system devices can be tracked and updated. System devices can be disabled, and device groups can be created.
Failure Notification
In terms of decent monitoring the system and device configuration, it can generate a failure logging in case of need. The failure notification can be tracked from both DASHBOARD and FAILURE NOTIFICATION page. Specify according to malfunction process, it can change to “On”, “Off”, “Ongoing” as well as delete the failure loggings
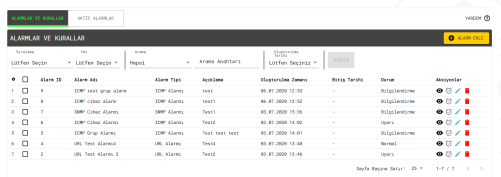
Alerts and Rules
Alarm templates, which threshold values are determined by user, can be generated for all monitored devices and systems.
alarms can be created with user-defined rules for single or multiple devices. Alarm conditions are evaluated when the device or system is triggered. Result of ensuring alarm conditions, the alarm template turns into an active alarm.
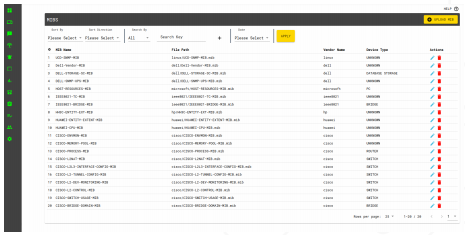
MIBs
MIB data of at least 500 devices that compatible with SNMP protocol are pre-defined in the software. SNMP data which is received from the device are compiled according to these MIBs. It is possible to create templates for devices which are not predefined, and so devices can be compiled by using created MIBs.
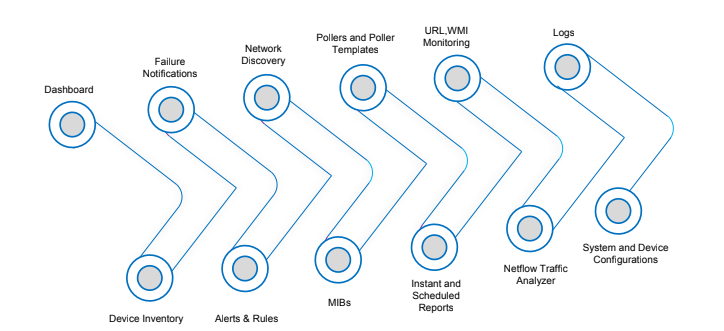
Logs
Event Log, System Log, and Trap Log can be monitored with the detailed information via servers.
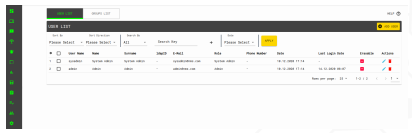
Users
With the Users Page, the new system user can be added, users can be edited and deleted. By creating user groups; system users can be assigned to the user groups.
Netflow Traffic Analyzer
Netflow Traffic Analyzer tool can receive traffic and usage details from the devices and the network and displays this information to the user graphically and numerically. SSH Terminal With the SSH commands, a secure encrypted connection is provided between two hosts over an ensecured network. This connection also capable of using for terminal access.
Detailed traffic information (package type, service type, traffic source, traffic target, data size, etc.) can be received from the desired ports of the devices and transmitted this information visually.
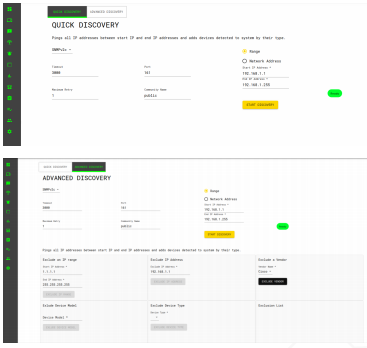
Network Discovery
The device is detected and/or device inventory information is updated by performing automatic and manual network discovery. In QUICK NETWORK DISCOVERY page; all IP Addresses in between entered start and ending IP range are scanned. Thereby, detected devices are registered in the system. In ADVANCED DISCOVERY page, desired IP Addresses can be exempted during the discovery.
Pollers
Timeout, retry, community alternatives for SNMP and ICMP poll operations that can be created for both global and custom groups. While Device/Device groups are automatically (periotic) or instantly polled; Disk Utilization, CPU Utilization, Memory Usage, Disk I/O Usage, arithmetic and logical operations are performed on the above values. During the polling process, device performance is not affected.
URL , WMI Monitoring
URL and WMI Performance is monitored so as to prevent potential threats on the network.
Reports
Predefined reports can be customized, and detailed reports are created for all monitored devices, systems and services with daily, weekly, monthly, and specified time range options. Reports can be exported as CSV, EXCEL, PDF, HTML formats and sent by email at the same time. Besides, reports can be scheduled depending on specified period in attempt to generate automatic repots.
SSH Terminal
With the SSH commands, a secure encrypted connection is provided between two hosts over an ensecured network. This connection also capable of using for terminal access.